In 2021 alone, 6 billion user accounts suffered data breaches, setting a new (not so happy) record for data breaches. 2022 was no better. The bottom line is that individuals and businesses must better protect themselves against cybercrime. The two most effective ways to safeguard sensitive information are strong passwords and multi-factor authentication (MFA). Together, they […]
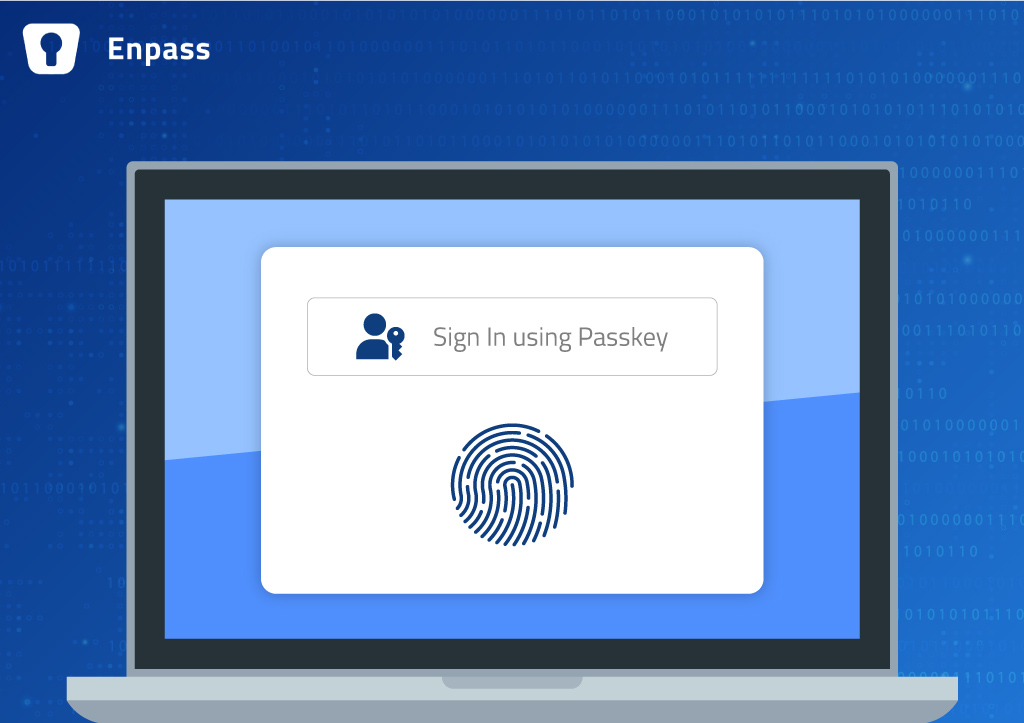
Google Introduces Passkeys: What Does That Mean for Password Managers?
Passwords are still widely used and will continue to be for some time. However, last year, Google made an important announcement in collaboration with the FIDO Alliance, Apple, and Microsoft. They expressed their commitment to supporting passkeys as an alternative to passwords, providing enhanced security and convenience. And yesterday, just in time for World Password […]
Start securing your digital lives on World Password Day
As we sign up for more and more online services every day, we have a forever increasing number of passwords and other credentials. With data breaches a common occurrence these days, it is pertinent to keep a regular check on your passwords. World Password Day – the first Thursday of May every year – is […]
Password Manager Breaches: Should You Worry as a User?
Disturbing reports of high-profile data breaches involving popular password managers have become more frequent. LastPass and Norton Password Manager were recently hacked, which has raised concerns about the security and reliability of using such tools to store sensitive information. These security breaches can naturally make anyone nervous about the safety of their data. But these […]
Safer Internet Day: Protecting People in the Digital Age
Safer Internet Day (SID) is celebrated each year in February to promote a safer and more positive use of digital technology. This globally recognized event addresses a wide range of concerns, from cyberbullying to social networking to digital identity, so that everyone uses technology responsibly, respectfully, and creatively. The safety issues in cyberspace have evolved […]
Enpass: The Ultimate LastPass Alternative, With the Freedom to Choose Where Your Data Is Stored
In December 2022, the popular cloud-based password manager LastPass revealed hackers had stolen the encrypted password vaults of its 30 million users. This means each user’s master password is now the only barrier between the hackers and all their private information. Most password managers, including LastPass, store users’ passwords in a centralized location — a […]