Uncover the critical differences between “types” of password managers and choose the one that best aligns with your enterprise security and compliance policies.
Choosing the right password manager for your business can be a daunting task. With many options available, it’s easy to get overwhelmed by the numerous promises and features. What organizations need is a solution that is secure, compliant, and truly effective in protecting them from breaches – not just providing a false sense of security.
Why?
The stakes are high, and the consequences of a misstep can leave your organization vulnerable to breaches and reputational damage, resulting in significant financial and operational losses.
Conversations with hundreds of CISOs and cybersecurity professionals reveal a common hurdle: despite recognizing the need for a password manager, many organizations struggle to make or enforce a decision, for fear of losing control and sovereignty of sensitive data. This prolonged indecision leaves organizations vulnerable to password-related breaches and associated risks.
Many organizations then dive straight into comparing individual products, based on functions, features and cost, without being aware of the underlying categories and differing architectures of password managers and their respective strengths and weaknesses.
To help navigate this complex landscape and understand what’s best for you and your organization’s needs, this article provides an in-depth comparison of the various categories of password managers, highlighting their key characteristics, Pros and Cons.
The three, no four types of password managers:
Most organizations choose from one of the following categories when it comes to password managers, and each category has its strengths and weaknesses.
Most good password managers run on all the key operating systems, support all the market leading browsers and deliver most of the same features and functions. Obviously, some have particular features that might be uniquely important to you and your organization. However, it’s the underlying architecture that is less well understood but defines the single biggest difference between the various vendor solutions and their true ability to meet all the requirements of your organization, in a secure and compliant manner.
1. SaaS-based password managers
SaaS-based password managers are the most commonly used solutions today, where your password data is fully under the control of the vendor. Everything, from your employees’ passwords to sensitive personal and business data, is stored centrally on the vendors’ servers.
Some prominent examples in this category are: LastPass, 1Password, and Dashlane.
Pros:
- Easy to use and accessible from anywhere with an internet connection.
- Centralized management with all advanced features like admin dashboards, vault sharing, and access recovery.
Cons:
- Data of all users is stored centrally on the vendors servers, making those servers a prime target for hackers, increasing the likelihood of large-scale breaches.
- Since the organization’s data is not stored within their own environment and control, this may lead to a break in corporate and regulatory policies regarding data security, privacy and sovereignty.
2. Self-hosted password managers
Due to the security, control over data location, and compliance concerns associated with SaaS-based password managers, many organizations turn to self-hosting as an alternative. Solutions such as Bitwarden, Passbolt provide self-hosted solutions, enabling organizations to host their password management infrastructure within their own environment.
However, it’s essential to understand the advantages and disadvantages of this approach:
Pros:
- Organizations have complete control over their data and where it’s stored, allowing them to choose from a range of hosting options, including on-premises servers, rented servers, or cloud services such as AWS, Azure and Google Cloud.
- Self-hosted solutions can be more attractive to businesses that already have the necessary infrastructure and trained IT teams with the right skills and expertise to manage and maintain the servers.
Cons:
- Deploying, managing, and maintaining these servers incurs additional costs and requires significant time, effort, and resources. Organizations need to have professionals with expertise in server management and security to ensure smooth operation, meet the uptime SLA of their server applications and manage all the updates and module compatibility issues.
- This solution still provides a single target for hackers, as all the organizations passwords are stored in one location, albeit within their own environment, thus meaning if a hacker breaches their server, they’ll likely to be able to access all the users’ passwords, etc.
3. Offline password management applications
These are the ‘old-school’ password managers, such as Keepass, that store all the passwords locally on the devices used by employees. No cloud, no data syncing between different devices—just good old-fashioned local storage.
Pros:
- The sole benefit of this approach is that sensitive data remains stored locally on the device, thereby minimizing the risk of a third-party breach and removing the risk of a mass breach.
Cons:
- These solutions do not give an organization the ability to manage, administer or support the use of the password managers, making it impossible to ensure compliance with the organizations policies
- Because the password data is stored locally, users do not have the convenience of securely sharing passwords through the password management application itself.
- Password data is not synchronized across devices, limiting access to sensitive information across multiple devices.
- If an employee’s device is lost or compromised, they will lose access to their password data and related systems and applications, resulting in major disruptions and inconvenience.
4. Best of all worlds approach
This is a whole new category where things get interesting (remember the 4th category we talked about at the start of this guide).
What if you could have all the “Pros” and none of the “Cons” described above?
A password manager that combines the convenience of a SaaS solution, without the loss of data sovereignty, corporate policy compliance and the risk of a mass breach, and the security and data sovereignty of self-hosted solution, minus the associated costs and resources required to deploy and manage them, and the risk of an organization wide breach.
Password Management YOUR way.
YOU control YOUR data, YOUR way, without the headaches of operating your own servers.
Interested?
That’s where Enpass, the decentralized password manager, comes in.
Enpass is the industry’s only password manager that allows organizations, rather than the vendor, to choose the location of their data. This means Enpass enables organizations to easily meet all their security, compliance, privacy, and data sovereignty requirements, when using a password manager.
Pros:
- Data stays within your preferred environment, such as Microsoft 365 or Google Workspace.
- No sensitive data is ever sent outside your environment to third-party vendor servers, ensuring greater security and regulatory compliance.
- This solution offers advanced administration features comparable to those of SaaS-based password managers, including the ability to manage users, set security policies, track adoption and password health across the company, enforce password-specific policies, monitor breaches and trigger password resets as required.
- No self-hosting pain – no additional server costs, server maintenance overheads and no need to worry about updates, patch management or application availability.
- Protection against mass breaches as data is not stored centrally on your own or third-party servers.
Cons:
- Security audit dashboard, secure vault sharing, and password recovery features of Enpass Business version are available for organizations that are using either Microsoft 365 or Google Workspace.
Comparison table – How does Enpass stack up?
To make it easier for you to compare, here’s a breakdown of how the different categories of password managers measure up against key features:
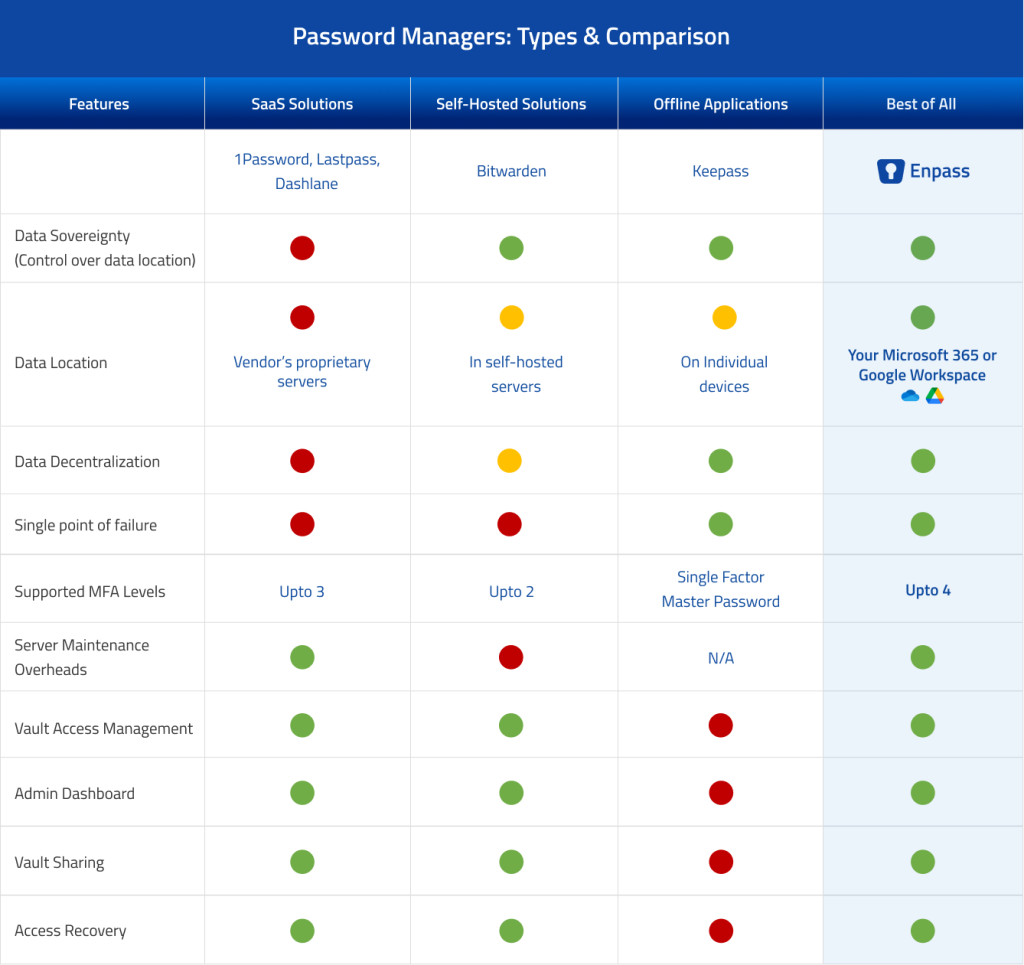
Password Manager Categories Comparison
As you can see, Enpass brings the best of all worlds together,
- offering all the control and security of a self-hosted solution without the headaches and costs of running your own servers or the risk of organization wide breaches, and
- all the extensive features of a SaaS-based solution without storing your data on the vendors cloud, outside your trusted environment, thus risking mass security and compliance breaches.
Affordable and flexible
Enpass is not only feature-rich but also incredibly affordable. With a variety of commercial options designed to meet the needs of businesses of all sizes—whether you’re just starting out or managing the security of a large enterprise.
The bottom line: Why Enpass is the smart choice
When it comes to choosing a password manager for your business, there’s a lot to consider—security, compliance, ease of use, and of course, cost. While SaaS solutions might seem convenient and offline managers feel secure, Enpass combines the best features of both, and more, giving you the security, control, flexibility, and compliance you need.
Ready to secure and control your data?
Watch this quick video to see how Enpass works and start a free trial to experience for yourself how Enpass can be the perfect password management solution for your organization.